You know that uneasy feeling when you hear about another major data breach? I get it. As someone who’s spent years helping businesses strengthen their cybersecurity, I’ve seen firsthand how two-factor authentication (2FA) can be a game-changer. But here’s the thing – not all 2FA methods are created equal. Let’s dive into what works, what doesn’t, and most importantly, what’s right for you.
Key Takeaways
- Multiple authentication factors provide significantly better protection than a username and password alone.
- One-time passwords generated by authenticator apps offer stronger security than SMS-based codes.
- Physical security keys provide the best defense against phishing attacks and credential theft.
- Biometric authentication eliminates the need to remember or manage multiple passwords while providing strong security.
- Using different types of factors (something you know, have, and are) is more secure than using multiple of the same type.
- Regular security audits and updates of your authentication credentials help maintain strong protection against evolving threats.
Understanding 2FA Basics
Picture this: you’re locking up your house. Using just a doorknob lock is like using only a password – it’s better than nothing, but not by much. Adding a deadbolt? Now that’s two-factor authentication in action! In the digital world, 2FA requires you to prove your identity in two different ways before gaining access to your accounts.
The beauty of 2FA lies in its three fundamental pillars:
- Something you know (like your trusty password)
- Something you have (think phone or security key)
- Something you are (those unique fingerprints of yours)
When you implement MFA or 2FA, you’re essentially adding extra layers of security to your digital fortress. While the difference between 2FA and MFA might seem confusing at first, it’s actually pretty simple: 2FA requires exactly two factors, while MFA can use multiple authentication methods.
Think of it this way: if someone manages to guess your password (something you know), they’d still need your phone (something you have) to complete the authentication process. It’s like having a backup goalkeeper – even if the first line of defense fails, you’ve got another one ready to make the save.
| Related: 15 Essential Ways to Protect Your Home Computer
Common 2FA Methods
Let’s break down the most popular authentication methods you’ll encounter in your digital journey. Each type of 2FA has its own personality – kind of like choosing between different types of locks for your house.
SMS-Based Authentication
This is probably the one you’re most familiar with. You know the drill – you try to log in, and boom, your phone buzzes with a text message containing a verification code. It’s like getting a secret handshake delivered right to your pocket.
| Pros | Cons |
|---|---|
| Wide availability | Vulnerable to SIM swapping |
| User-friendly | Requires cell service |
| No app needed | SMS interception risks |
| Quick setup | Less secure than alternatives |
| Familiar to users | Network dependency |
Authenticator Apps
Think Google Authenticator or Authy – these apps are like having a tiny security guard in your pocket, constantly generating new codes to keep your accounts safe.
| Pros | Cons |
|---|---|
| Works offline | Requires smartphone |
| More secure than SMS | Setup complexity |
| Time-based codes | Device dependency |
| No network needed | Risk of phone loss |
| Multiple account support | Initial learning curve |
Biometric Authentication
Now we’re getting fancy! Using biometric data like your fingerprint or iris scan feels like something out of a spy movie, doesn’t it?
| Pros | Cons |
|---|---|
| Highly secure | Hardware requirements |
| Quick access | Privacy concerns |
| Can’t be forgotten | Can’t be changed |
| User convenience | Cost implications |
| Unique to user | Backup method needed |
Security Keys
These physical authentication devices are the heavyweight champions of 2FA security. They’re like having a mini Fort Knox that fits on your keychain.
| Pros | Cons |
|---|---|
| Maximum security | Additional cost |
| Phishing-resistant | Physical dependency |
| No network needed | Limited compatibility |
| Simple to use | Risk of loss |
| FIDO2 support | Learning curve |
Implementation Considerations
Let’s get real for a minute. Choosing the right authentication method isn’t just about picking the most secure option – it’s about finding what works for your specific situation. Just like you wouldn’t install a bank vault door on your garden shed, you need to match the security level to your needs.
For businesses, this means thinking about:
- Compliance requirements (because nobody likes failing audits)
- User experience (because security isn’t helpful if nobody uses it)
- Implementation costs (because budgets matter)
- Training needs (because change can be challenging)
And for individual users? Consider:
- Your comfort with technology
- The value of what you’re protecting
- Your daily usage patterns
- Backup options (because things go wrong)
Remember, the best authentication method is the one that you’ll actually use consistently. Don’t let perfect be the enemy of good!
| Related: Data Protection vs Data Privacy: Key Differences Explained
Best Practices
Listen, I’ve seen enough authentication disasters to last a lifetime. Let me share some hard-earned wisdom about implementing multi-factor authentication that’ll save you some headaches. Think of these as your security golden rules.
First things first: mix it up! Using two knowledge factors (like a password and a security question) is like wearing two paper masks – it might feel like double protection, but you’re still vulnerable to the same type of attack. Instead, combine different factors for maximum security. It’s like having both a lock and an alarm system – they protect you in completely different ways.
Here’s what I recommend for a solid authentication strategy:
- Layer Your Defense
- Start with a strong password (and yes, “password123” doesn’t count!)
- Add a possession factor like an authenticator app
- Consider biometric authentication for sensitive operations
- Implement out-of-band authentication for high-risk transactions
- Plan for Problems
- Set up backup authentication methods (trust me, you’ll thank me later)
- Store recovery codes in a secure location
- Keep your authentication apps updated
- Document your recovery process
- Regular Security Audits
- Review your authentication methods quarterly
- Update security policies based on new threats
- Monitor for suspicious authentication attempts
- Test your recovery procedures
Future Trends
Hold onto your security keys, folks, because the future of authentication is looking pretty wild! As someone who’s been in the cybersecurity trenches, I’m genuinely excited about where this technology is heading.
Emerging Authentication Technologies
The passwordless authentication revolution is coming, and it’s bringing some fascinating innovations:
- Behavioral Biometrics Remember how your mom could tell it was you typing on the family computer? Modern systems can do the same thing! They analyze patterns in how you:
- Type on your keyboard
- Move your mouse
- Hold your phone
- Interact with apps
- Adaptive Authentication Think of this as a smart bouncer for your digital life. It adjusts security requirements based on:
- Your location
- Device type
- Time of day
- Activity patterns
- Risk level
- Continuous Authentication Instead of just checking your identity at login, these systems keep verifying you’re really you throughout your session. It’s like having a really attentive security guard who doesn’t just check your ID at the door but keeps an eye on you the whole time.
| Related: Top Ways to Protect Your Personal Information and Privacy
Making the Right Choice
At this point, you might be thinking, “Great, but which authentication method should I actually use?” Let me break it down for you.
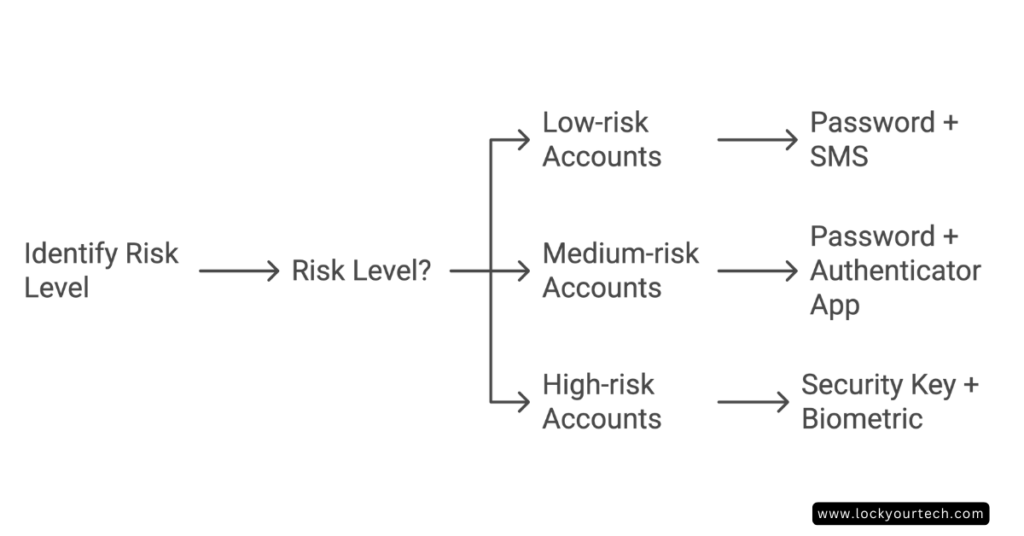
For Personal Use:
- Low-risk accounts (news sites, forums): Password + SMS authentication
- Medium-risk (email, social media): Password + authenticator app
- High-risk (banking, crypto): Security key + biometric authentication
For Business Use:
- Small businesses: Authenticator apps with backup SMS
- Medium enterprises: Mix of methods based on role sensitivity
- Large corporations: Hardware security keys + biometric data
Remember, the goal isn’t to build Fort Knox (unless you’re actually Fort Knox). It’s to find the right balance between security and usability that best suits your needs.
Conclusion
Let’s wrap this up with some real talk: yes, implementing two-factor authentication might feel like extra work. But in today’s digital world, it’s like wearing a seatbelt – that minor inconvenience could save you from a major disaster.
Whether you choose SMS verification, an authenticator app, biometric authentication, or a security key, any 2FA is better than no 2FA. Start with something simple, get comfortable with it, and then level up your security game as needed.
Remember: cybersecurity isn’t about being perfectly secure (spoiler alert: nothing is). It’s about being secure enough to protect what matters while still being able to actually use your stuff.
So, what’s your next move? Take a look at your most important accounts and start with one. Trust me, future you will be grateful for the extra protection.
Frequently Asked Questions
What are the main differences between MFA, 2FA, and 2SV?
While these authentication methods might seem similar, they serve different purposes. 2FA requires exactly two factors, while MFA offers flexibility with multiple authentication methods. 2SV (two-step verification) often uses the same type of factor twice, making it less secure than true multi-factor authentication. MFA is a more secure option as it combines various authentication types like biometrics, token-based authentication, and password authentication protocols.
How does biometric authentication compare to traditional 2FA methods?
Biometric authentication provides a higher level of security than traditional password-based authentication since it uses unique physical characteristics. Unlike methods that require something the user remembers or carries, biometric data is always available and can’t be forgotten or lost. However, it typically needs to be combined with another authentication factor for complete authentication security.
What are the pros and cons of using SMS-based 2FA?
SMS authentication is widely used because it’s familiar and doesn’t require special apps. However, it’s vulnerable to SIM swapping and interception. While it’s better than single sign-on (SSO) alone, authentication apps like Google Authenticator offer better security. SMS works best as an additional authentication method rather than your primary security measure.
How does Google Authenticator integrate with third-party services?
Google Authenticator uses standardized authentication protocols to generate time-based one-time passwords. It integrates with various services through QR codes or manual keys, making it compatible with most platforms that support authenticator apps. The authentication involves using these temporary codes as a second factor, working alongside your regular password authentication.



