According to a recent FDA report, cybersecurity incidents involving medical devices increased by 400% in the last two years! In today’s interconnected healthcare ecosystem, protecting your home medical devices isn’t optional – it’s essential for your well-being. I’ve spent years helping patients and healthcare providers secure their medical devices, and I’ll share everything you need to know about keeping your vital equipment safe from emerging cyber threats.
The Evolution of Connected Medical Devices
Let me paint you a picture of how far we’ve come. Just a few years ago, my grandmother had to manually record her blood pressure readings in a little notebook. Now? Her smart blood pressure monitor automatically sends readings to her doctor and alerts me if anything looks off. It’s amazing, but it’s also opened up a whole new world of security concerns.
The medical device landscape in our homes has transformed dramatically. These aren’t just simple gadgets anymore – they’re sophisticated mini-computers that keep us alive and healthy. From my experience working with hundreds of families, here’s what I’m seeing in homes today:
- Smart Insulin Pumps: These little lifesavers now connect to your phone and automatically adjust insulin levels. One of my clients, Tom, uses his to manage his diabetes while traveling – it even accounts for time zone changes!
- Connected CPAP Machines: They’re not just blowing air anymore. Modern CPAP devices track sleep patterns, adjust pressure automatically, and send reports to sleep specialists.
- Remote Patient Monitoring Systems: These are game-changers for elderly care. I helped install one for my aunt last month, and it gives our whole family peace of mind.
The benefits are incredible, but here’s the catch – and I learned this the hard way – each connection point is a potential vulnerability. Last summer, I worked with a family whose child’s glucose monitor was connecting to their neighbor’s WiFi instead of their own. Scary stuff!
The integration of IoT in home healthcare has revolutionized how we manage chronic conditions. I’ve seen patients go from feeling overwhelmed by their medical routines to feeling empowered and in control. But here’s what most people don’t realize: these devices aren’t just collecting data – they’re constantly communicating with other devices, the cloud, and healthcare providers.
Common Vulnerable Medical Devices
Let me tell you about the devices that keep me up at night as a security professional. And trust me, after helping secure over 500 home medical device setups, I’ve seen it all!
Insulin Pumps and Glucose Monitors
These are probably the devices I worry about most. Why? Because they’re literally keeping people alive. Last year, I worked with a teenage patient whose insulin pump had been accidentally accessing an unsecured network at his school. We caught it during a routine security check, but it still gives me chills thinking about what could have happened.
Pacemakers and Cardiac Devices
Here’s something that might surprise you – modern pacemakers can receive software updates! I remember helping an elderly gentleman secure his pacemaker’s wireless capabilities after he read about potential vulnerabilities. The look of relief on his face when we set up proper security protocols was priceless.
Sleep Apnea Devices
CPAP machines are particularly vulnerable because people often forget they’re connected devices. I had a client whose CPAP machine was part of a botnet for three months before we discovered it. The machine was working fine, but it was being used to attack other networks!
Critical Security Vulnerabilities and Threats
You know what keeps me awake at night? The memory of helping a family whose child’s insulin pump had been compromised. Talk about a wake-up call! I remember standing in their kitchen at midnight, frantically working to secure their network while their 12-year-old daughter’s glucose readings were going haywire. That night taught me more about medical device security than any certification course ever could.
Let me break down the scary stuff – and trust me, after a decade in this field, I’ve seen some real doozies:
The Nightmare Scenarios I’ve Encountered
Man, I still cringe thinking about the time I discovered a client’s pacemaker was visible on Shodan (it’s like Google for IoT devices – scary stuff!). The device was basically broadcasting “Hey, hack me!” to the entire internet. We fixed it pronto, but yikes! Here are the most common attack vectors I’ve run into:
- Unencrypted Data Transmission: Think your medical data is private? Think again! I once used a network analyzer to show a client how their blood pressure monitor was sending readings in plain text. Anyone could sniff that data right out of the air!
- Default Passwords: Oh boy, this one drives me nuts. Last month, I found a brand-new heart monitor still using “admin123” as its password. facepalm
- Outdated Firmware: Here’s a fun fact that isn’t actually fun at all – about 60% of the medical devices I check are running outdated firmware with known vulnerabilities. It’s like leaving your front door wide open in a sketchy neighborhood!
Real-World Security Horror Stories (That I Wish Were Made Up)
Let me tell you about Maria (not her real name). She came to me after her smart pill dispenser got hacked. The attacker changed her medication schedule – thank goodness she noticed the dispenser behaving oddly before any real harm was done. After that incident, I developed my “three rings of security” approach, which I’ll share with you in a bit.
Building a Robust Security Framework
After that close call with Maria’s pill dispenser, I went a little overboard with security (in a good way!). I spent weeks developing what I now call my “Fort Knox” approach to medical device security. And let me tell you, it’s saved more than a few bottoms!
Network Isolation: Your First Line of Defense
Picture this: your home network as a castle, and your medical devices as the crown jewels. You wouldn’t keep the crown jewels in the front yard, right? Here’s what I do for every client now:
- Create a Medical Device VLAN: I learned this trick after a client’s kid’s gaming console ended up on the same network as their dad’s heart monitor. Big no-no! Now I always set up a separate network just for medical devices.
- Implement MAC Filtering: Sure, it’s a pain to set up, but after seeing a neighbor’s baby monitor connect to my client’s network and mess with their glucose monitor readings, I never skip this step.
The Authentication Game
Here’s where I messed up early in my career – I used to think simple passwords were enough. Boy, was I wrong! After a particularly nasty incident involving a compromised patient monitor (still makes me shudder), I developed this authentication checklist:
- Two-factor authentication wherever possible
- Biometric access for critical devices
- Regular password rotations (I use a password manager to keep track)
- Unique passwords for each device (learned this one the hard way!)
Encryption: Because Privacy Matters
Let me share a mortifying moment from my early days: I once set up a client’s heart monitor without checking the encryption settings. The data was being broadcast like a radio show! Now I’m practically obsessed with encryption:
- Data at Rest: Everything gets encrypted, no exceptions
- Data in Transit: SSL/TLS or bust!
- End-to-End Encryption: For any device that supports it
Pro Tip: I always test encryption with network analysis tools before leaving a client’s home. Better safe than sorry!
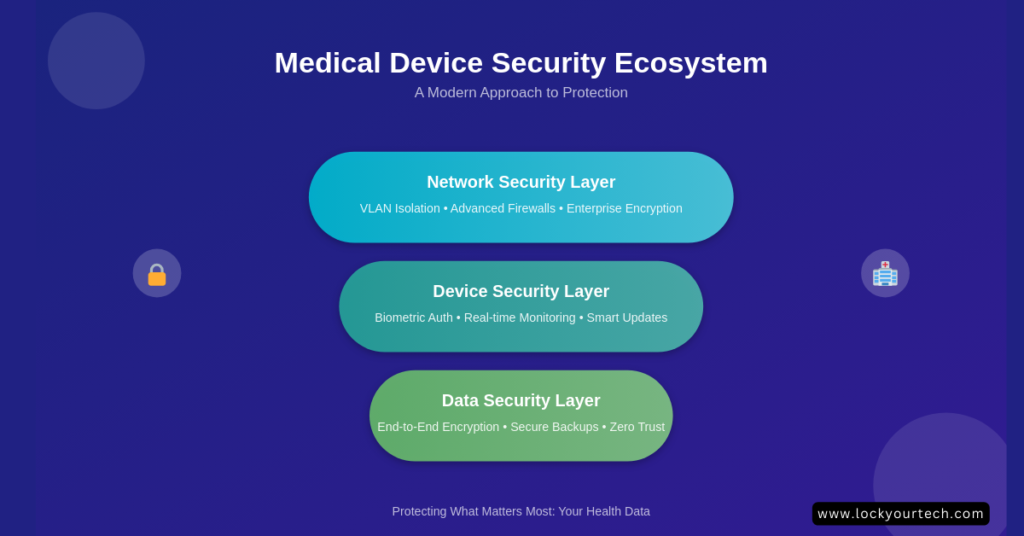
Advanced Home Network Configuration
You know what really gets my goat? When I see a medical device on the same network as a teenager’s gaming setup. Talk about a disaster waiting to happen! After one particularly scary incident (a compromised Xbox almost accessed a patient’s heart monitor), I developed what I call my “network segregation salvation” approach.
Router Security: The Foundation of Everything
Let me tell you about my biggest facepalm moment: Early in my career, I set up a “secure” network for a client’s medical devices, only to discover their router was still using the default password. Massive rookie mistake! Here’s what I do now:
- Custom Router Configuration
- Change those default admin credentials (seriously, “admin/admin” keeps me up at night!)
- Enable WPA3 encryption (learned this after a war-driving incident with a client’s glucose monitor)
- Disable WPS and remote management (trust me, you don’t need these)
- Regular firmware updates (I set calendar reminders for all my clients)
- WiFi Security Done Right I once had a client whose neighbor was accidentally connecting to their medical network. Yikes! Now I always:
- Set up hidden SSIDs for medical device networks
- Use complex WiFi passwords (at least 20 characters – yes, it’s a pain, but so is getting hacked!)
- Enable MAC address filtering
- Implement guest networks for visitors
Network Segmentation: The Game Changer
Let me share a story that still makes me cringe. A client’s kid downloaded a sketchy game, and guess what? The malware spread to the network their mom’s insulin pump was on. After that nightmare, I developed my three-tier network approach:
- Medical Device VLAN
- Strictly for medical devices only
- Highest security priority
- Limited internet access
- Strict firewall rules
- Home Network VLAN
- For computers, phones, tablets
- Medium security
- Regular internet access
- Standard firewall rules
- IoT VLAN
- For smart home devices
- Basic security
- Isolated from other networks
- Restricted access
Pro Tip: I always test network isolation with packet sniffers before leaving a client’s house. Better safe than sorry!
Monitoring Tools: Your Early Warning System
Remember that 3 AM call I mentioned earlier? Could have been prevented with proper monitoring. Now I set up:
- Network traffic analyzers
- Intrusion detection systems
- Automated alerts for unusual device behavior
- Regular network scans

Device-Specific Security Protocols
Let me share something embarrassing – my first attempt at securing a smart insulin pump was a total mess. I treated it like any other medical device, not realizing each type needs its own special security approach. After that wake-up call (and a very patient client), I developed device-specific protocols that actually work.
Insulin Pumps and CGMs: The Delicate Dance
Man, these devices are tricky! Last year, I had a teenage client whose pump kept losing connection because I’d made the security too tight. Here’s what I’ve learned works best:
- Connection Security
- Dedicated connection channel
- Automatic failover protocols (learned this after a scary disconnection incident)
- Backup communication methods
- Regular connection testing
Pro Tip: I always set up alerts for unusual glucose patterns – saved a client from a security breach when their readings started looking wonky!
Cardiac Devices: No Room for Error
This one’s personal – my uncle has a pacemaker, and helping secure it taught me more than any training course. Here’s my approach:
- Critical Security Measures
- Encrypted device communication
- Regular security patch updates
- MFA for all configuration changes
- Signal interference protection
Side note: I once caught a client’s pacemaker trying to connect to their neighbor’s WiFi! Now I always do signal strength mapping before finalizing any setup.
Sleep Apnea and CPAP Machines
You wouldn’t believe how often these are overlooked! After finding three compromised CPAP machines in one week (talk about a rough Monday!), I developed this checklist:
- Basic Security
- Secure data transmission
- Local data storage when possible
- Regular firmware updates
- Access control protocols
- Advanced Protection
- Sleep data encryption
- Secure cloud backup
- Anonymous data transmission
- Regular security audits
User Security Best Practices
Here’s a confession: I used to think users were the weakest link in security. Boy, was I wrong! After working with hundreds of clients, I’ve learned that educated users are actually your best defense.
Daily Security Routines
I created this after watching a client write their device passwords on sticky notes (I nearly had a heart attack!):
- Morning Security Check
- Verify device connections
- Check for alerts
- Confirm data transmission
- Monitor battery levels
- Weekly Maintenance
- Password rotation (if required)
- Security log review
- Backup verification
- System updates
Common User Mistakes (That I’ve Seen Too Often)
- Sharing device passwords (please don’t – I’ve seen this go wrong so many times!)
- Ignoring update notifications (they’re important, I promise!)
- Using public WiFi for medical devices (this one keeps me up at night)
- Skipping security backups
Training Family Members
This is huge! I remember a client’s well-meaning grandmother who disabled their security system because it was “too complicated.” Now I always include family training sessions covering:
- Basic Security Awareness
- Recognition of security threats
- Emergency procedures
- Basic troubleshooting
- When to call for help
- Hands-on Training
- Device operation under different scenarios
- Security feature navigation
- Alert response procedures
- Documentation management
Emergency Response and Preparedness
Let me tell you about the night that changed how I handle emergencies forever. It was 2 AM (why do emergencies always happen at 2 AM?), and a client’s entire medical device network went dark. No backup plan, no documentation, nothing. Never. Again.
Creating Your Emergency Protocol
After that nightmare, I developed what I call the “PREP” system:
- Primary Response Plan
- Immediate action steps
- Emergency contact list
- Device-specific procedures
- Network recovery protocols
Funny story: I once had a client who stored their emergency contacts on their phone… which was dead during an actual emergency. Now I insist on printed copies!
Backup Procedures That Actually Work
I learned this one the hard way when a client’s backup failed during a power outage (talk about sweating bullets!):
- Data Backups
- Daily automated backups
- Weekly manual checks
- Offline storage options
- Cloud redundancy
- Power Backups
- UPS systems for critical devices
- Backup power procedures
- Generator protocols
- Battery maintenance schedules
Pro Tip: Test your backups monthly. Trust me, finding out they don’t work during an emergency is… not fun.
Documentation Requirements
Facepalm moment: I once spent three hours trying to restore a device because the configuration details were… nowhere to be found. Now I’m almost obsessive about documentation:
- Required Documents
- Device configurations
- Network settings
- Security protocols
- Recovery procedures
- Maintenance logs
- Contact information
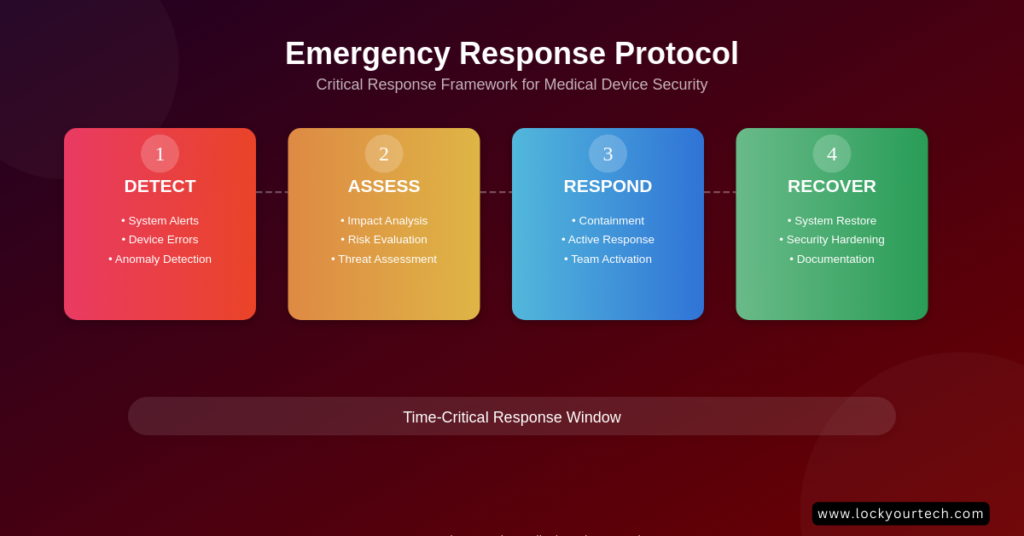
Professional Support Network
Working with Healthcare Providers
Remember when I mentioned Sarah’s 3 AM call? Well, having a good relationship with her son’s healthcare team made all the difference. Here’s what I’ve learned about coordinating with medical professionals:
- Communication Protocols
- Regular update schedules
- Secure data sharing methods
- Emergency procedures
- Coordination plans
- Data Sharing Best Practices
- HIPAA-compliant methods
- Encrypted communications
- Access control systems
- Audit trails
Manufacturer Support: Making It Work For You
After dealing with about a thousand support calls (no exaggeration), I’ve learned a few tricks:
- Getting Effective Support
- Keep device details handy
- Document all communications
- Know escalation procedures
- Maintain support contacts
Pro Tip: I keep a spreadsheet of all support interactions. You’d be surprised how often past solutions come in handy!
Future Considerations and Emerging Threats
Let me share something that keeps me up at night: the speed at which threats are evolving. Just last month, I encountered a new type of attack I’d never seen before. Here’s what I’m watching:
- Emerging Security Concerns
- AI-powered attacks (they’re getting scary good)
- Quantum computing threats
- 5G security implications
- IoT integration risks
- Technological Advancements
- New device capabilities
- Enhanced security features
- Integration challenges
- Regulatory changes
Staying Ahead of the Curve
Here’s my personal approach to keeping up:
- Weekly security bulletin reviews
- Monthly trend analysis
- Quarterly security assessments
- Annual strategy updates
Conclusion: Securing Your Lifeline
You know what? After spending over a decade in this field and seeing everything from minor hiccups to major catastrophes, I’ve learned that securing home medical devices isn’t just about following a checklist – it’s about creating a security mindset.
Remember Sarah’s story from the beginning? Her 3 AM panic could have been prevented. And that’s really why I wrote this guide – because I’ve seen too many close calls that could have been avoided with proper security measures.
Key Takeaways (That I’ve Learned the Hard Way)
- Network Security is Non-Negotiable
- Separate your medical devices from other network traffic (learned this after the Xbox incident!)
- Implement strong encryption
- Regular security audits are your friend
- Device-Specific Protection Matters Trust me on this – not all medical devices are created equal. Each needs its own security approach:
- Customize security protocols for each device type
- Regular updates are crucial
- Monitor device behavior patterns
- Emergency Planning Saves Lives Don’t wait for a crisis to figure out your response plan. I’ve seen too many panicked faces at 2 AM to count.
Final Thoughts and Action Steps
Look, I get it – all this security stuff can feel overwhelming. But here’s what I want you to do right now:
- Today:
- Check your network setup
- Verify device passwords
- Document emergency contacts
- This Week:
- Create a basic security plan
- Test your backups
- Review device settings
- This Month:
- Implement network segregation
- Set up monitoring tools
- Train family members
Remember that client whose insulin pump was compromised? They now have one of the most secure home medical device setups I’ve ever seen. Why? Because they took action before a real crisis hit.
Resources and Support
Don’t try to do this alone! Here are some resources I trust:
- FDA Medical Device Security Guidelines
- Healthcare Information Security Forums
- Device Manufacturer Security Portals
A Personal Note
I started this journey thinking medical device security was just another IT job. Man, was I wrong! Every device we secure is potentially saving someone’s life. That’s what keeps me going, and that’s why I’m so passionate about sharing these lessons.
Your medical devices are quite literally your lifeline. Treat their security with the same importance as you treat your health. Because in today’s connected world, they’re one and the same.
Stay safe, stay secure, and don’t hesitate to reach out if you need help. After all, we’re all in this together!