The number of internet-connected devices in the average home has skyrocketed in recent years. While the convenience of smart home tech is undeniable, this explosion of IoT (Internet of Things) devices has also created new security vulnerabilities. Hackers are constantly on the lookout for ways to infiltrate home and small business networks, and one of their favorite tactics is to gain access through rogue, unauthorized devices.
If you want to keep your network safe, it’s essential to be able to detect and remove any unauthorized devices trying to connect. In this guide, we’ll walk you through the steps to monitor your network, identify suspicious activity, and shut down intrusions before they can cause damage.
Understanding Network Visibility and Security
At the core of network security is the concept of “trusted” versus “unauthorized” devices. A trusted device is one that you’ve explicitly approved to access your network, like your family’s laptops, smartphones, and smart home gadgets. An unauthorized device, on the other hand, is any system trying to connect that you haven’t explicitly granted access to.
Maintaining full visibility over every device on your network is crucial. Hackers are always looking for vulnerabilities, and unsecured or unknown devices provide the perfect entry point. By proactively monitoring your network, you can quickly detect and eliminate any rogue devices before they can wreak havoc.
Tools To Detect Unauthorized Devices on Network
There are several effective tools you can use to maintain visibility and control over your home or small office network. Let’s explore the top options:
1. Network Monitoring Software
Specialized network monitoring solutions like PRTG, Nagios, and Zabbix provide powerful capabilities to detect unauthorized devices. These free, open-source tools can automatically scan your network, identify connected systems, and alert you to any new or suspicious activity.
When setting up a network monitoring tool, be sure to enable features like device discovery, asset tracking, and alert customization. This will allow you to quickly spot unknown systems trying to join your network.
2. Network Scanning Tools
In addition to ongoing monitoring, you should also perform regular network scans to get a comprehensive view of all the devices connected. Free tools like Angry IP Scanner and Nmap are excellent options for this task.
These scanners will provide detailed information about each connected system, including its IP address, MAC address, and device type. By comparing the results to your known, approved devices, you can easily identify any rogue systems.
3. Router/Firewall Dashboards
Don’t overlook the built-in security features of your home or small office router. Most modern networking equipment provides an administrative dashboard where you can view detailed information about connected devices and network activity. This is one of the easiest way to detect rogue devices on your network.

Take some time to explore your router’s web interface. Look for sections that list all the systems currently accessing your network, and review them regularly for any unfamiliar entries. Many routers also allow you to set alerts for new device connections, which can be a valuable early warning system.
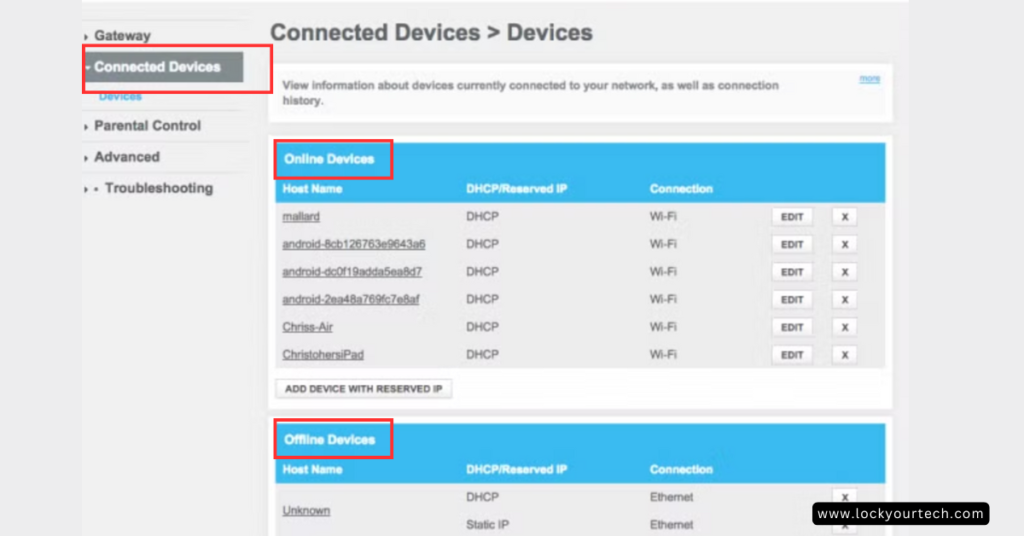
Identifying Unauthorized Devices
Now that you have the right tools in place, how do you actually spot unauthorized devices on your network? Here are some key things to look for:
- Unknown Device Names: When reviewing your network devices, be on the lookout for any systems with generic, non-descriptive names like “Unknown” or “Router123.” These are often indicators of rogue hardware.
- Suspicious MAC Addresses: MAC addresses are unique identifiers assigned to network interface cards. If you see any MAC addresses that don’t match your known devices, that’s a red flag. Consider implementing MAC address filtering.
- Unusual Activity Patterns: Monitor your network for spikes in bandwidth usage, data transfers, or login attempts from unfamiliar systems. These can be signs of unauthorized access.
- Devices That Don’t Fit Your Profile: Take a close look at any systems that seem out of place on your network, like an unrecognized smart home gadget or a laptop that doesn’t belong to your family.
Responding to Unauthorized Access
If you do detect an unauthorized device on your network, it’s important to act quickly to mitigate the potential damage. Here’s a step-by-step process for handling the situation:
- Isolate the Rogue Device: The first priority is to cut off the intruder’s access. Depending on how the device is connected, you can block it at the firewall or router level, disable the relevant network port, or remove it from your wireless network.
- Investigate the Intrusion: Dig deeper into the network logs to understand how the unauthorized device gained access and what it may have done while connected. This information will help you shore up your security defenses.
- Secure Your Network: Take immediate steps to secure your network and prevent similar intrusions in the future. This may include changing Wi-Fi passwords, implementing more granular access controls, or updating the firmware on your networking equipment.
Ongoing Network Monitoring Best Practices
Detecting and responding to unauthorized devices is an ongoing process, not a one-time task. To keep your network safe, make the following best practices a regular part of your security routine:
- Regularly Scan for New/Changed Devices: Schedule periodic network scans to identify any new systems or changes to existing devices.
- Review Network Activity Reports: Examine your monitoring tools’ logs and alerts for any suspicious behavior or unrecognized connections.
- Set Alerts for Suspicious Activity: Configure your network security tools to notify you whenever new, unknown devices attempt to join your network.
- Educate Users on Security Protocols: Ensure everyone accessing your network, from family members to employees, understands the importance of network security and their role in maintaining it.
By following these steps and leveraging the right monitoring tools, you can significantly enhance the security of your home or small office network. Proactive vigilance is key to keeping unauthorized devices at bay and protecting your digital assets.
Last updated: November 2024
Author’s Note: Network security is an ever-evolving landscape. Stay informed, keep your tools and devices updated, and remain diligent in monitoring your network. The safety of your data depends on it.